How to Clean a Hacked WordPress Website
Is my website hacked? is not a question that starts from a hunch – when your website gets hit, it’s pretty clear. But it’s not a question exclusively for WordPress website administrators either – all websites can get hacked, no matter the platform they’re built on.
Nevertheless, since this popular open-source CMS is specifically vulnerable to certain attacks, our topic for today will be just that: how can you tell that your WordPress site was hacked and, even more important, how to clean a hacked WordPress website.
Maybe you’re not there, yet, and you’re clueless on why you should even worry about this possibility. And the truth is that a malicious attack can make your website lose not just its search engine rankings, but also the confidence of its users. Don’t let your online reputation perish this way – protect your website and the people who use it!
Here’s what you should do:
Clean your hacked WorPress site – practical guide for web developers
DETECT THE PROBLEM
When malicious code sneaks in, symptoms may vary:
- The website no longer works optimally, with server errors, illegitimate links, and weird Google search results showing up;
- The website topic changes, with redirects to inappropriate websites, flashy ads to adult products, and strange characters from other languages showing up;
- The access to the admin section is blocked or the website itself can no longer be accessed at all.
Whatever is going wrong, the following steps are just as essential as identifying the problem.
CHANGE ALL YOUR PASSWORDS
No matter if you can still access your admin account or not, the first actionable step is to reset your password!
Tip: Can’t enter your account? Bypass the login screen and access the database through phpMyAdmin or Adminer. Once you’re in, go to wp_users and change your login details from there.
- Set new passwords for all access points, be it FTP/SFTP, Admin, CPanel, MySQL or another panel you are using.
- Do it for both the admin account and all the other accounts.
- Ideally, use a password generator to create long, complex, and unique passwords.
- Don’t forget to also change the secret keys – as long as cookies are valid, the hacker remains logged in and you can cut off its access by getting new values from the WordPress key generator and overwriting them into the wp-config.php file.
Change the login details/password of your WordPress website
CONDUCT A THOROUGH INVESTIGATION
Now that you changed your passwords, you can focus on the actual investigation:
Address the issue to your hosting provider – it might be a simple failure of hosting service or an actual attack. Either way, the provider should be able to inform you, especially if other websites hosted by them have recently experienced similar problems.
Test the local environment to find a potential source of infection attack – most often the local machine is also infected with a malware or virus so scanning it with at least two different antiviruses is essential.
Test the website for specific traces of an attack – access it from different devices, use the Fetch as Google function, make comparisons with previous versions, unhide all files and folders and analyze them:
- Use different devices and different types of devices, to analyze and compare results.
- Go to the Google Search Console and look for specific notification emails from Google.
- Use the Fetch as Google function to see if and how the Googlebot can access your website and what it renders: from Google Search Console > Crawls > Fetch as Google > Fetch and Render.
- Use the current files to compare them with the ones from previous back-ups and see if there are any notable differences.
- Sort files by size and look for any potentially malicious code lesser than 5MB, usually an executable file.
- Scan all the data and delete the viruses, the worms or the autoruns that you find.
- Focus on the root of your website (.htaccess or index.php files) and the wp-content/themes directory (index.php, functions.php, header.php or footer.php) where most malicious redirects nestle in.
Think of the most vulnerable points of your website – what security plug-ins you have installed or you are actually missing, how often you change your passwords and how complicated these passwords are etc.
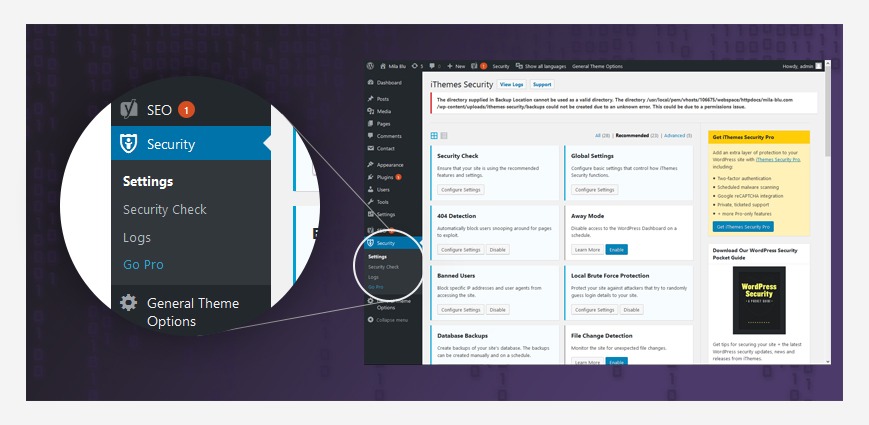
RUN SOME SECURITY PLUG-INS
To see exactly what you’re dealing with and know how to clean your hacked WordPress website, make use of some powerful security plug-ins. iThemes and WordFence should be your go-to resources, allowing you to scan the website and get a detailed report on the problems discovered and the files or folders that have been recently modified or replaced.
Both plug-ins are extremely helpful not only with assessing the current situation of your website but also with enhancing its protection once the attack was fixed:

Security plug-ins for WordPress
With iThemes, for instance, you have access to file change and 404 detections, brute force protection, strong password enforcement, hiding login & admin (on the standard version) as well as online file comparisons and changing WordPress salts & keys (on the pro version).
With WordFence, on the other hand, you get to scan your website up to the tiniest details, getting a thorough report of all the problems discovered. In this way, you will know exactly where and what files or folders have been modified or replaced. Moreover, you will also know what updates you should make to the theme and to the existing plug-ins, just to enhance their security.
GET TO THE ACTUAL CLEANING, STEP-BY-STEP
Now that you are well-aware of the problem and you know what you’re dealing with, you will have to clean the website:
- Begin by installing a clean WordPress from scratch;
- Copy the website theme;
- Reinstall the clean plug-ins or copy the existing ones, BUT only after you’re sure there’s nothing suspicious in their code;
- Activate iThemes and change your admin username and password AGAIN;
- Change passwords for all your access points: FTP/SFTP, Admin, CPanel, MySQL etc., as well as the secret keys, overwriting these new values into the wp-config.php file;
- Check the database to be sure there’s nothing suspicious in there – especially if had problems with the Google redirect, chances are it was a file problem;
- Check the Upload folders and make sure you have exclusively image files in there, no .php files;
- Deactivate the WP-Admin link;
- Rerun a security check and make sure all results are good;
- Reuse the Fetch as Google function and compare results;
- Do a Google search and see what results you get, if and how you can access your website;
- Run a full back-up so you won’t have to go through the entire above next time your WordPress website gets hacked!
Cleaning a hacked WordPress website, STEP-BY-STEP
FOR THOSE WHO DON’T HAVE A WORDPRESS WEBSITE…
Make no mistake, even websites built on other platforms, be it Joomla, Magento, Drupal etc, can be affected by malicious attacks. Especially if the website has a WordPress blog, chances are that a virus will find its vulnerable points, get to the website through the blog, and create some killer backdoors, modifying the .htaccess files.
That’s why you need to always be vigilant and invest in your website security:
- Change passwords more often
- Set an additional password to your Admin directory
- Limit the number of login attempts
- Run periodic security checks
- Setup a website firewall together with a monitoring system
- Disable the Theme & Plugin editors
- Keep plug-ins and themes up to date
If you’re not sure what to do or where to start from, ask help from professionals! Flowmatters is here to help you with the entire above!
Drop us a note and we’ll discuss how we can help.
From safely backing up your current website to doing all the necessary efforts to clean your hacked website, we have what it takes to make your life easier and to protect your online business!